Instant Disaster Recovery
Businesses now face more threats than ever before. you can easily secure clients’ data
and quickly return to a production-ready state in case of any disruption.
Rapidly recover from cyberattacks and other unplanned outages
Get back up running in mere minutes by spinning up IT systems in the Cloud with full site-to-site connectivity and the ability to recover them to similar or dissimilar hardware
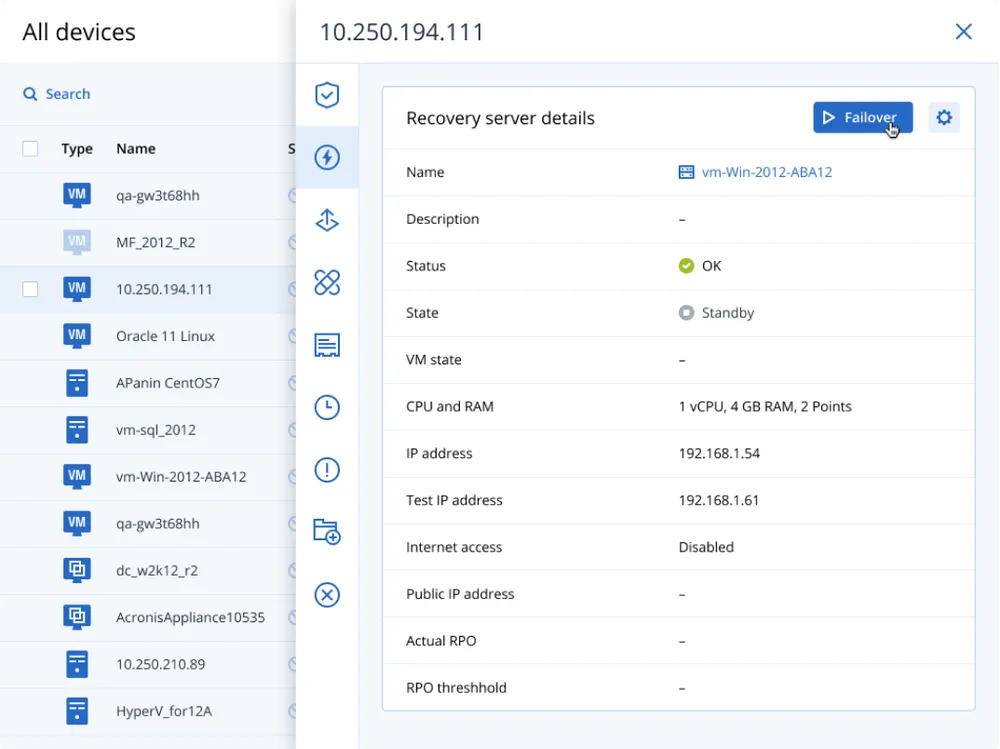
Fast recovery
No matter the cause of the unplanned downtime, our disaster recovery technology ensures you achieve both RPOs and RTOs that are under 15 minutes.
With the RunVM engine, you get near-instant production and test failover speeds, while flexible backup frequency policies can help you offer tighter RPOs.
Three-click setup
Skip the additional hardware and installation and set up your disaster recovery plan in three clicks.
Choose between multiple templates with different configurations of recovery servers, enabling you to set up disaster recovery plans quickly and easily.
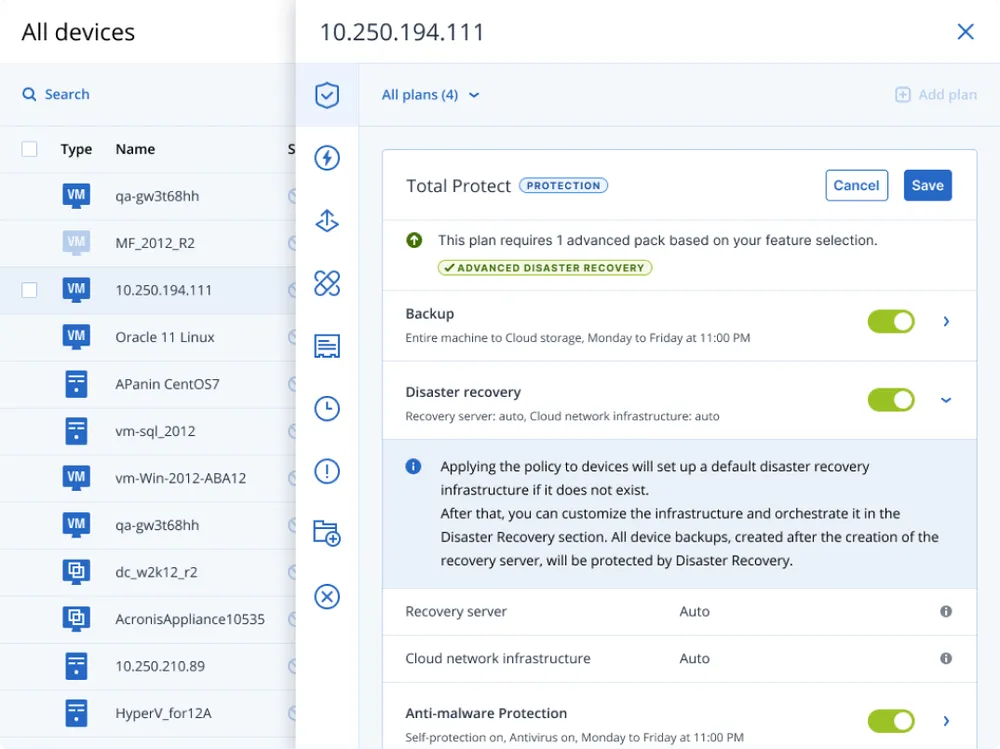
Easy management
No need to add, learn, or manage another platform. Easily configure server lists, test connectivity settings, configure disaster recovery orchestration with runbooks, and recover on multiple networks.
Features
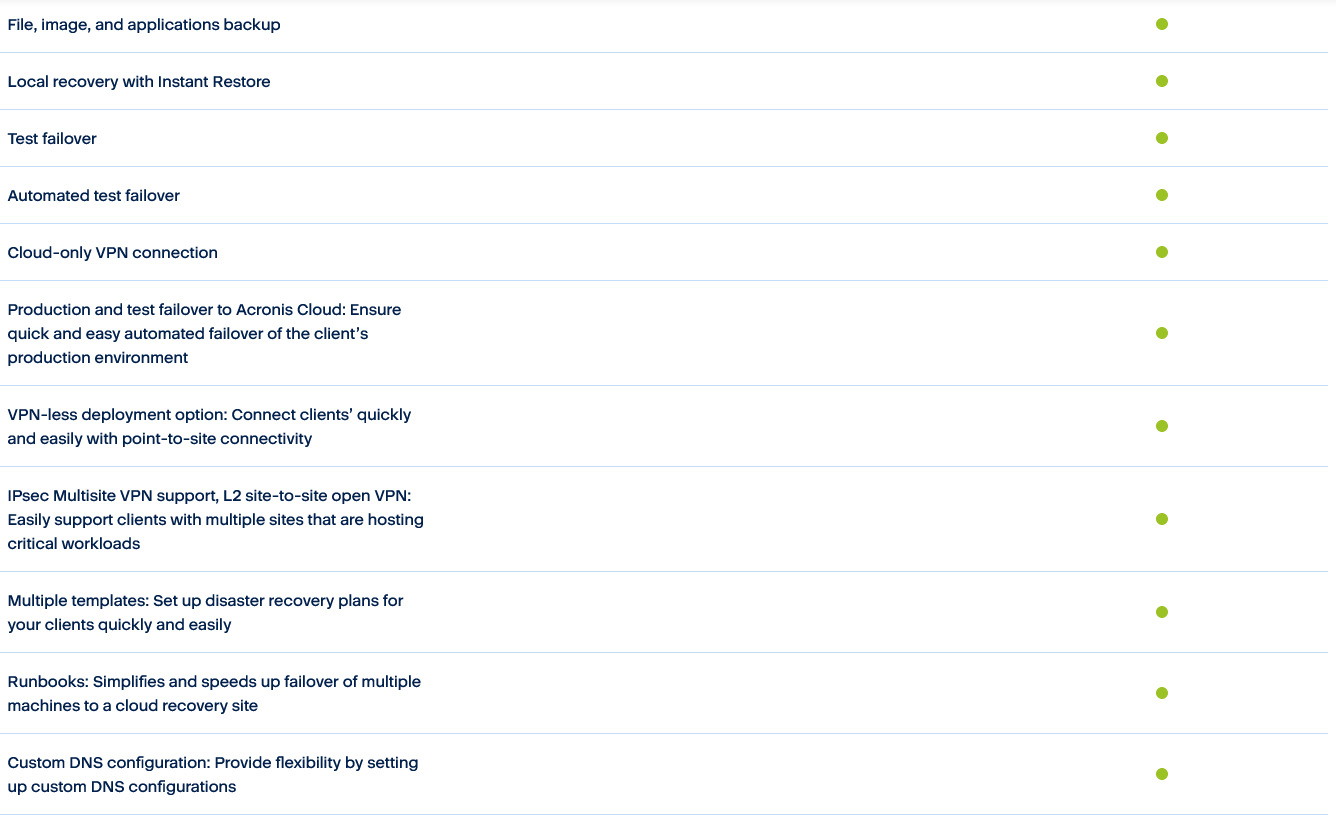
One solution for any workload

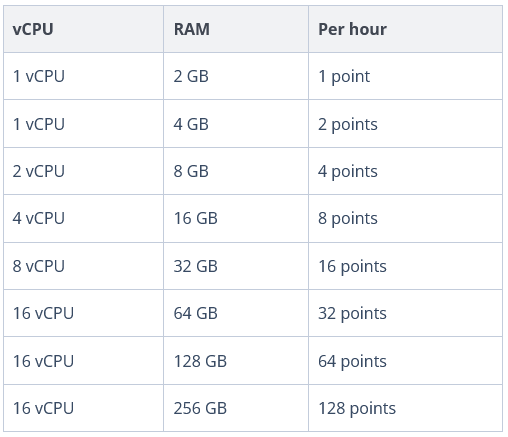
How compute points are consumed in Disaster Recovery Add-on
Compute points is a currency used to achieve the necessary performance of the running failover server.
Available licenses can include 100, 200, 400, 800, 1000. 2000 Compute Points.
Compute Points license does not have the expiration date on its own, but is effective while Disaster Recovery Storage Subscription License is valid.
For example, with 1 license pack containing 500 compute points, you can run a failover server with 8 vCPU and 32 RAM for 31 hours and 15 minutes.
If you don’t have enough points for a full hour, time will be calculated in proportion to available compute points.
How compute points are consumed
Disaster recovery for physical and virtual workloads
Minimize downtime by enabling easy, scalable and efficient cloud based recovery of all popular workloads including Windows and Linux physical servers and VMs, major hypervisors, and Microsoft apps.
Production failover
Ensure quick and easy automated failover of the client’s production environment to an offsite server running in the Disaster Recovery Storage or to a hot storage in the Cloud.
Automated test failover
Save time and effort with a simplified, automated test failover. With the Advanced Disaster recovery, you can perform scheduled test failover for any server on a monthly basis, giving you the confidence that you can recover quickly and successfully.
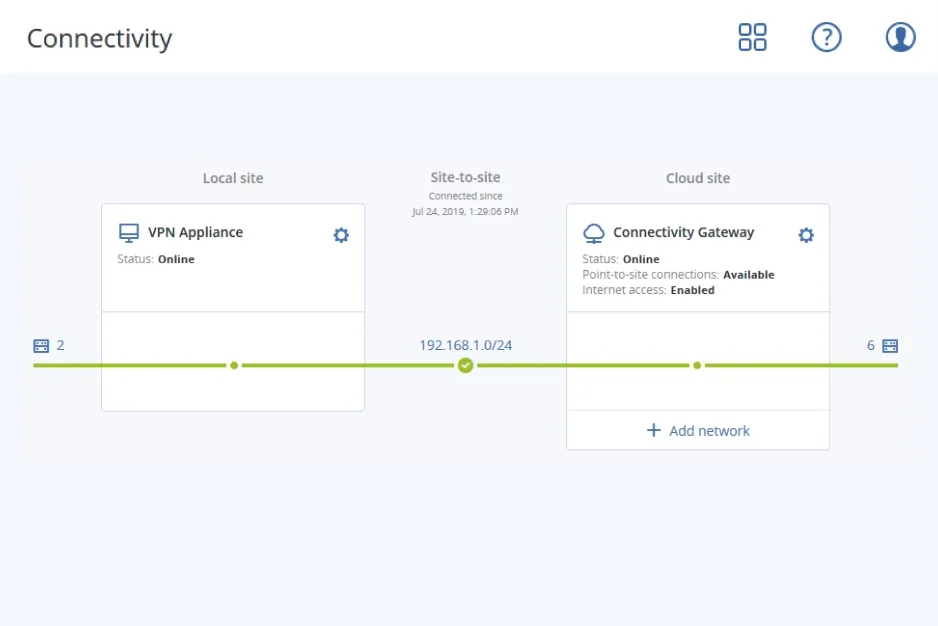
Site-to-site VPN connection
Enable secure VPN connection between the client’s local site and the cloud site to facilitate partial failover of tightly dependent servers on the local site. When one of the servers is recreated on the cloud site, the servers continue to communicate, ensuring minimal downtime.
Test Disaster Recovery Readiness
Perform DR testing in an isolated environment to confirm application availability, ensure compliance, and prove DR readiness — without any impact on production systems.
Execution monitoring
Gain visibility into disaster recovery orchestration with a detailed runbook-execution real-time view and execution history.
Point-in-time recovery
Prevent data loss and avoid data corruption with granularity of control over data protection and recovery capabilities. Restore systems and data to any recoverable point in the past, instead of to the latest one.
IPsec multisite VPN support
Strengthen security with IPSec multisite VPN support that integrates secure protocols and algorithms, so you can easily support clients with multiple sites that are hosting critical workloads with higher requirements for security, compliance and bandwidth.
Custom DNS configuration
Create custom DNS configurations for disaster recovery cloud services in the cloud. This enables you to easily adjust DNS settings for your clients – making it even easier for you to support them.
Endpoint Detection and Response
In the face of increasing attack sophistication, volume, and pace, driven by AI, organizations require a complete security framework – to identify, protect, detect, respond, and recover.
Instead of counting on a costly & complex stack of point solutions, with native integration of endpoint detection & response, endpoint management, and backup & recovery, completedr streamlines security capabilities across a comprehensive, integrated security framework, delivering the industry’s most complete security solution.
The most complete EDR solution: comprehensive protection across NIST
Unlike pure-play cybersecurity solutions, Cyber Protect Cloud brings the full power of its platform with integrated capabilities across leading cybersecurity framework, like the NIST for unmatched business continuity.
- Integrated backup and recovery capabilities, providing unmatched business continuity where point-security solutions fail
- Streamlined single-click remediation and recovery
- Complete, integrated protection across the NIST security framework — Identify, Protect, Detect, Respond, and Recover — all from a single solution
Endpoint Detection and Response
Identify
You need to know what you have to fully protect it, and investigate into it. Our platform includes both inventory and data classification tools to better understand attack surfaces.
Protect
Close security vulnerabilities using our threat intelligence feed, forensic insights, and natively integrated tools across the broader comnpletedr platform like data protection maps, patch management, blocking analyzed attacks, and policy management.
Detect
Continuous monitoring for security related events using automated behavioral- and signature-based engines, URL filtering, an emerging threat intelligence feed, event correlation and MITRE ATT&CK®.
Respond
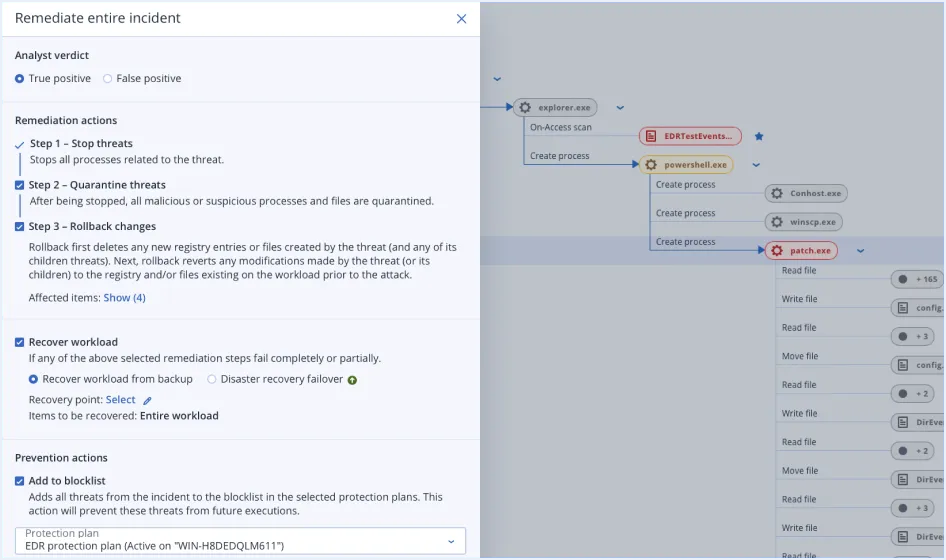
Investigate suspicious activities and conduct follow-up audits using a secure, remote connection into workloads or reviewing automatically saved forensic data in backups. Then, remediate via isolation, killing processes, quarantining, and attack-specific rollbacks.
Recover
Ensure systems, endpoint data and the client business are up and running using our fully integrated, market-leading backup and disaster recovery products and solutions.
Flexible Pricing Plans
We help protect businesses when needed the most with Instant Disaster Recovery
and Fully Encrypted Cloud Backups to get you back up and running as fast as possible.
Cloud Backup
- 15-second recovery time
- Ransomware protection
- Military-grade encryption
- Redundant backups
- Cloud access in just 3 clicks
Disaster Recovery
- Support for all platforms
- Production failover
- Site-to-site VPN connection
- Disaster Recovery Readiness
- Automated test failover
Fully Managed
- 100% Fully Managed
- Backups & Disaster Recovery
- We take the pain away
- Protect your entire Business
- Receive Daily Reports
